For people who think this is fake, please read descriptionfor people who think this is real, will read descriptionand watch the whole video-. The new method to crack WPA/WPA2 enabled WiFi networks that allow attackers to access Pre-shared Key hash that used to crack Passwords used by targeted victims. This Method found during the attack against the recently released WPA3 security standard which is extremely harder to crack since its used Simultaneous Authentication of Equals (SAE), a.
- What Is A Wpa2 Password For Mac
- How To Retrieve Wifi Password Windows 10
- How To Hack Wpa2 Wifi Password Using Cmd Windows 10
As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords, coWPAtty. In this tutorial, we’ll use the piece of software developed by wireless security researcher Joshua Wright (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords. It is easier than you think, so let’s get to it!
Step 1: Find the Cowpatty
Cowpatty is one of the hundreds of pieces of software that are included in the BackTrack [Download] and Kali [Download] OS’s. If you are using a different Distro, you can download and install coWPAtty Here. For this demo, I will be using BackTrack. For some reason in BackTrack, it was not placed in the /pentest/wireless directory, but instead was left in the /usr/local/bin directory, so let’s navigate there.
cd /usr/local/bin
Because cowpatty is in the /usr/local/bin directory and this directory should be in your PATH, we should be able to run it from any directory in BackTrack.
Step 2: Find the Cowpatty Help Screen
To get a brief rundown of the cowpatty options, simply type:
cowpatty

BackTrack will provide you a brief help screen. Take a note that cowpatty requires all of the following:
- a word list
- a file where the password hash has been captured
- the SSID of the target AP
Step 3: Find the AP
Just as in cracking with aircrack-ng, we need to put the wireless adapter into monitor mode.
airmon-ng start wlan0
Now, look at the available APs using the monitor interface and airodump:
airodump-ng mon0
leave this screen by hitting CTRL+C
Step 4: Start a Capture File
Next, we need to start a capture file where the hashed password will be stored when we capture the 4-way handshake.
airodump-ng –bssid 00:25:9C:97:4F:48 -c 9 -w cowcrack mon0
This will start a dump on the selected AP (00:25:9C:97:4F:48), on the selected channel (-c 9) and save the the hash in a file named cowcrack.
Step 5: Capture the Handshake
Now when someone connects to the AP, we’ll capture the hash and airdump-ng will show us it has been captured in the upper right-hand corner. Some people just wait for a computer to connect. Other people send DEAUTH packets to kick them off the wifi, and then they automatically connect again, at which time you will capture the handshake. I may cover this tomorrow or the next day.
Step 6: Run the Cowpatty

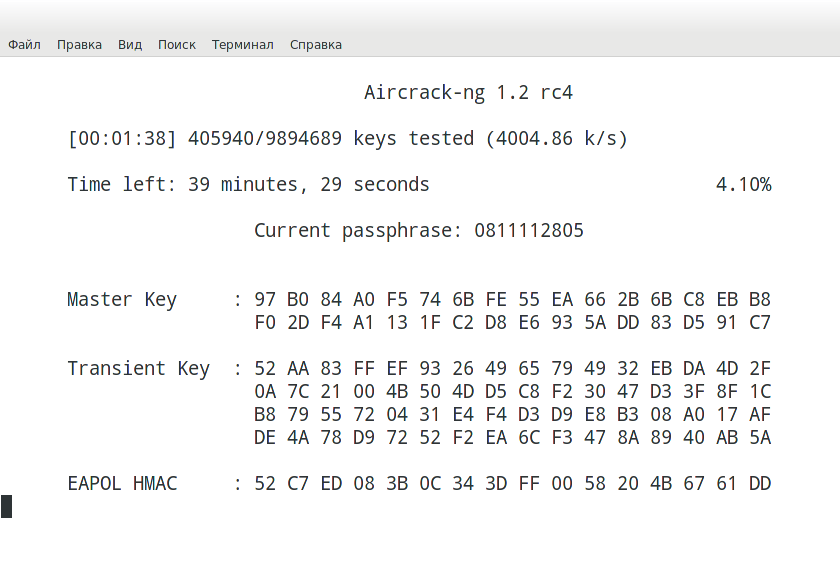
Now that we have the hash of the password, we can use it with cowpatty and our wordlist to crack the hash.
cowpatty -f /pentest/passwords/wordlists/darkc0de.lst -r /root/cowcrack-01.cap -s Mandela2
As you can see in the screenshot above, cowpatty is generating a hash of every word on our wordlist with the SSID as a seed and comparing it to the captured hash. When the hashes match, it dsplays the password of the AP.
Step 7: Make Your Own Hash
Although running cowpatty can be rather simple, it can also be very slow. The password hash is hashed with SHA1 with a seed of the SSID. This means that the same password on different SSIDs will generate different hashes. This prevents us from simply using a rainbow table against all APs. Cowpatty must take the password list you provide and compute the hash with the SSID for each word. This is very CPU intensive and slow.
Cowpatty now supports using a pre-computed hash file rather than a plain-text word file, making the cracking of the WPA2-PSK password 1000x faster! Pre-computed hash files are available from the Church of WiFi [ Link ], and these pre-computed hash files are generated using 172,000 dictionary file and the 1,000 most popular SSIDs. As useful as this is, if your SSID is not in that 1,000, the hash list really doesn’t help us. Plus rainbow tables are Gargantuan to download!
In that case, we need to generate our own hashes for our target SSID. We can do this by using an application called genpmk. We can generate our hash file for the “darkcode” wordlist for the SSID “Mandela2” by typing:
genpmk -f /pentest/passwords/wordlists/darkc0de.lst -d hashes -s Mandela2
Step 8: Using Our Hash
Once we have generated our hashes for the particular SSIDs, we can then crack the password with cowpatty by typing:
cowpatty -d hashfile -r dumpfile -s ssid
Stay Tuned for More Wireless Hacking Guides
Keep coming back for more on Wi-Fi hacking and other hacking techniques!
After the long holiday, first I want to say Merry Christmas and Happy new year 2014 to you. Today we will learn about 5 Steps Wifi Hacking – Cracking WPA2 Password. A lot of readers send many request regarding how to crack wireless WPA2 password in our request tutorial page.
According to Wikipedia :

Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access II (WPA2) are two security protocols and security certification programs developed by the Wi-Fi Alliance to secure wireless computer networks. The Alliance defined these in response to serious weaknesses researchers had found in the previous system, WEP (Wired Equivalent Privacy)
A flaw in a feature added to Wi-Fi, called Wi-Fi Protected Setup (WPS), allows WPA and WPA2 security to be bypassed and effectively broken in many situations. Many access point they have a Wifi Protected Setup enabled by default (even after we hard reset the access point).
Requirements:
1. Wireless card (support promiscuous mode)
In this tutorial I use ALFA AWUS036H from Amazon.
2. Access point with WPA2 and WPS enables
5 Steps Wifi Hacking – Cracking WPA2 Password:
1. Open our terminal (CTRL+ALT+T) and type airmon-ng (view tips and tricks how to create keyboard shortcut on kali linux)
this command will lists our wireless card that attached with our system.
2. The next step we need to stop our wireless monitor mode by running airmon-ng stop wlan0
3. Now we ready to capture the wireless traffic around us. By running airodump-ng wlan0 our wireless interface will start capturing the data.
What Is A Wpa2 Password For Mac
From the picture above, we can see many available access point with all the information. In the green box is our victim access point which is my own access point 🙂
Information:
BSSID (Basic Service Set Identification): the MAC address of access point
PWR: Signal level reported by the card.
Beacons: Number of announcements packets sent by the AP
#Data: Number of captured data packets (if WEP, unique IV count), including data broadcast packets.
#/s: Number of data packets per second measure over the last 10 seconds.
CH: Channel number (taken from beacon packets).
MB: Maximum speed supported by the AP. If MB = 11, it’s 802.11b, if MB = 22 it’s 802.11b+ and higher rates are 802.11g.
How To Retrieve Wifi Password Windows 10
ENC: Encryption algorithm in use.
CIPHER: The cipher detected. TKIP is typically used with WPA and CCMP is typically used with WPA2.
AUTH: The authentication protocol used.
ESSID: Shows the wireless network name. The so-called “SSID”, which can be empty if SSID hiding is activated.
4. From the step 3 above, we can find access point with encryption algorithm WPA2 and note the AP channel number. Now we will find out whether target AP has WPS enabled or not.
wash -i wlan0 -c 8 -C -s
if the WPS Locked status is No, then we ready to crack and move to step 5.
5. The last step is cracking the WPA2 password using reaver.
How To Hack Wpa2 Wifi Password Using Cmd Windows 10
reaver -i <your_interface> -b <wi-fi victim MAC address> –fail-wait=360
Because we already get the information from step 3 above, so my command look like this:
reaver -i wlan0 -b E0:05:C5:5A:26:94 –fail-wait=360
it took about 5 hours to crack 19 characters WPA2 password (vishnuvalentino.com) from my Kali virtualBox, but it depend with our hardware and wireless card.
Conclusions:
1. WPA and WPA2 security implemented without using the Wi-Fi Protected Setup (WPS) feature are unaffected by the security vulnerability.
2. To prevent this attack, just turn off our WPS/QSS feature on our access point. See picture below (I only have the Chinese version 😛 )
Notes: Only practice this tutorial on your own lab and your own device. Hacking can be a crime if you don’t know where to put it.
Share this article if you found it was useful:
Blogger at hacking-tutorial.com. Love PHP, offensive security and web. Contact him at me[-at-]vishnuvalentino.com
See all posts by Vishnu Valentino || Visit Website : http://www.vishnuvalentino.com